
Scammers caught on MetaMask complaint, arrest of identity thief from the 90s, and other cybersecurity events.


We have collected the most important news from the world of cybersecurity for the week.
- Cryptocurrency scammers exposed themselves by complaining about MetaMask actions.
- A 33-year-old US resident impersonated someone else.
- An attack on the supply chain of XZ Utils affected popular Linux distributions.
- 250 citizens of India freed from cyber ransom.
Cryptocurrency scammers complain about MetaMask actions
Phishing site operators, mimicking the self-destructing message service privnote.com, inadvertently revealed the extent of their cybercriminal activities involving cryptocurrency wallet spoofing. Journalist Brian Krebs reports this.
In March, they complained to MetaMask developers about the supposed improper labeling of their site privnote[.]co as malicious. This was despite the evidence provided by the Ethereum wallet security team.
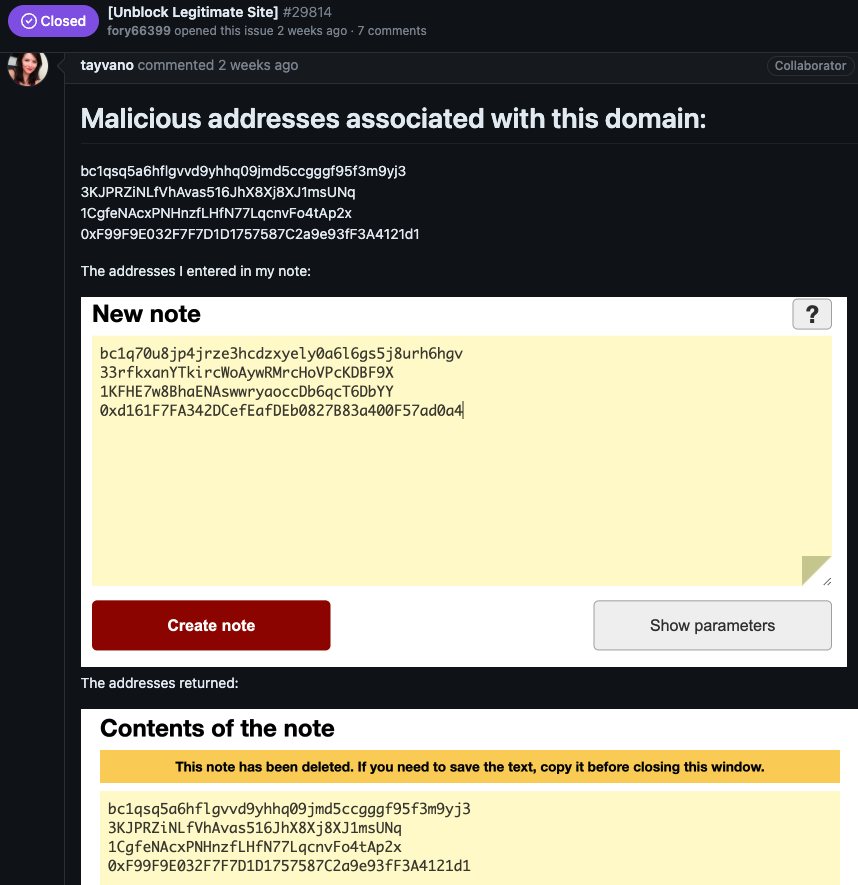

While communicating with the MetaMask support team, the criminals provided several more domains used for spoofing Privnote.
Analysis led cybersecurity researchers to two individuals – Andrey Sokol from Moscow and Alexander Ermakov from Kyiv. Most likely they are aliases.
Since 2020, they have registered numerous phishing sites, including those mimicking MetaMask and stealing user credentials from various darknet marketplaces.
Just one of these platforms from March 15 to 19, 2024, brought the criminals around $18,000 in cryptocurrencies.
33-year-old US resident impersonated another person
System administrator Matthew Keirans from Iowa had been living under the name of his acquaintance, William Woods, since 1990. The Register reports this.
Keirans obtained fake documents, including a birth certificate from Kentucky, a social security number, and an I-9 form, which he used to join the IT team at an Iowa University hospital in 2013. Using the new ID, he opened a bank account in Colorado and took out multiple loans.
In 2019, the real Woods, who was homeless at the time, discovered a loan taken out in his name for $130,000. However, when he went to the bank, he couldn’t answer the security questions to access the account.
Woods provided his genuine social security card and California ID, but he was ultimately accused of identity theft. Under the name of “Matthew Keirans,” he spent nearly a year and a half in prison and six months in a psychiatric hospital.
In 2023, the real Woods found the hospital where the fraudster worked. The hospital management hired a private detective, and with a DNA test, the truth was revealed.
Matthew Keirans pleaded guilty. He faces up to 32 years in prison and a $1.25 million fine.
Supply chain attack on XZ Utils affects popular Linux distributions
Unknown hackers, in a two-year supply chain attack, introduced a serious backdoor into the popular XZ Utils utility set. On March 29, 2024, the problem was accidentally discovered by Microsoft PostgreSQL developer Andrey Froind, who noticed unusual computer freezing.
The XZ Utils library is used for lossless data compression and working with the .xz format. The malicious code made its way into popular Linux distributions, albeit mostly in their beta versions.
The presence of the backdoor has already been confirmed by developers of Fedora, Debian, openSUSE, Kali Linux, Gentoo, and Arch Linux distributions. Package managers Homebrew and embedded OS OpenWrt were also affected.
Github banned accounts of suspects and closed access to malicious repositories.
Users are recommended to roll back XZ Utils version to 5.4.6 or 5.4.2. Additionally, the company Binarly has released a public scanner for detecting the implant in any Linux binary file.